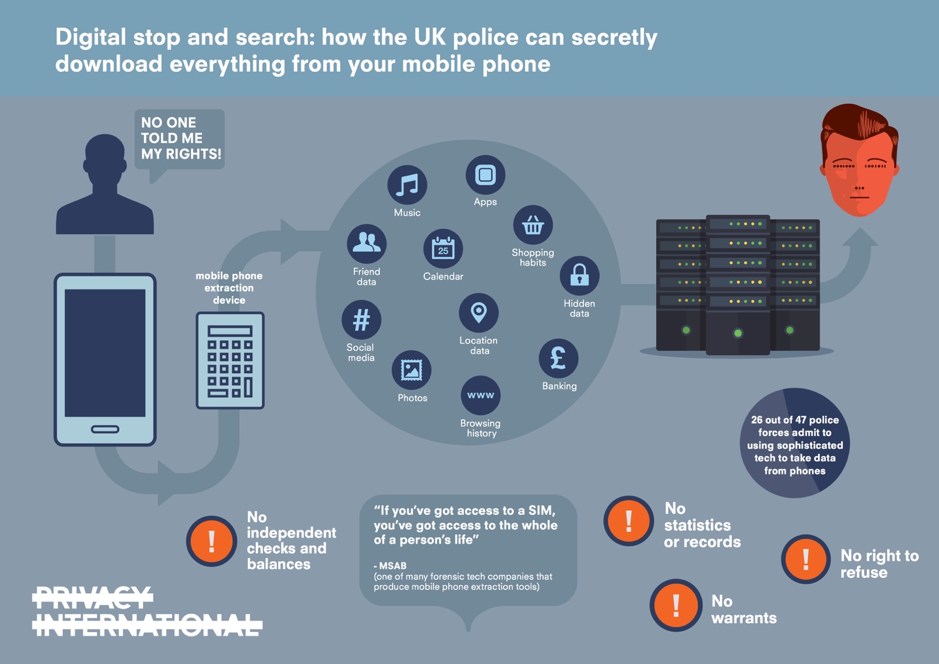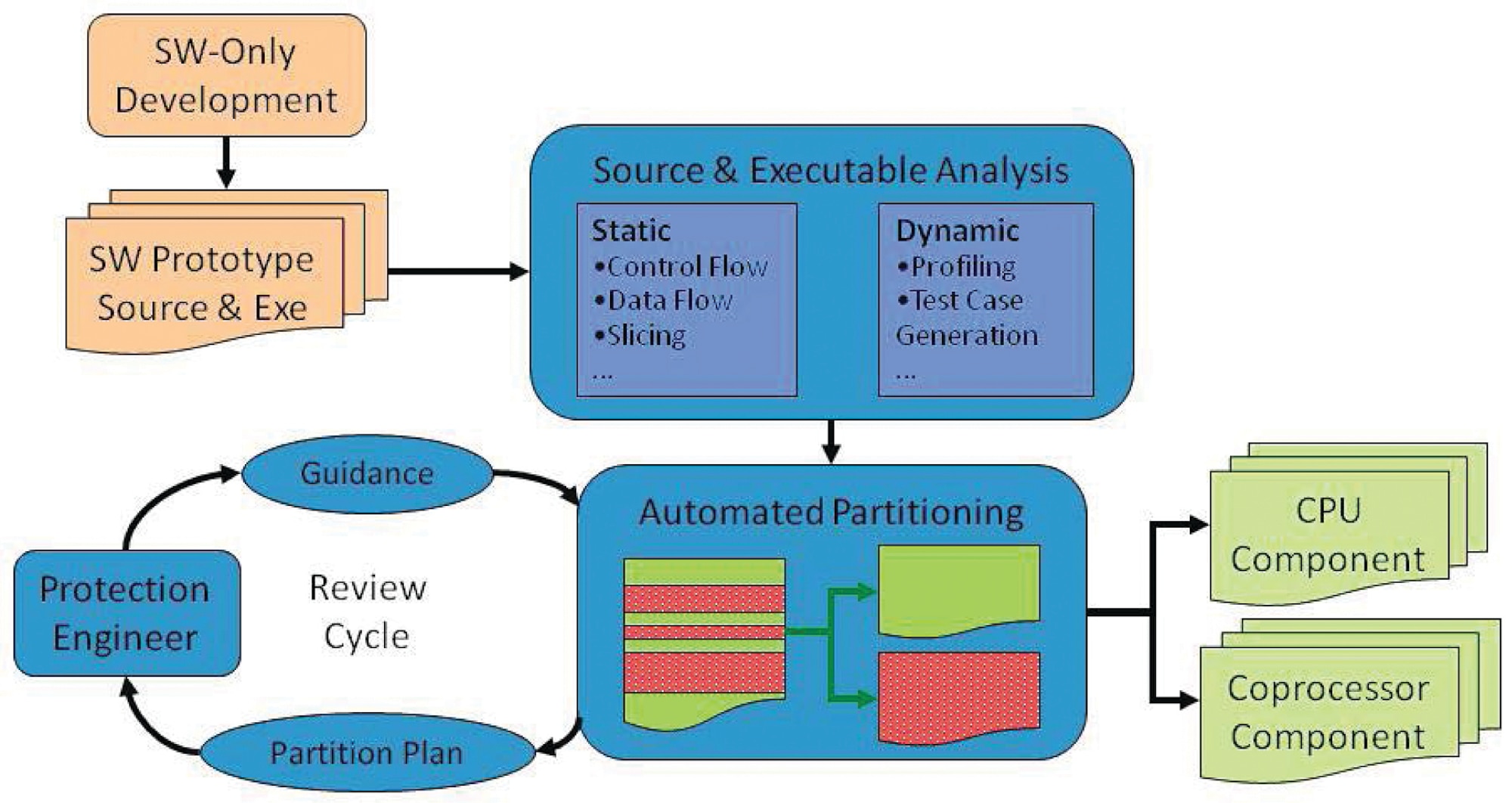
Software Protection to Deter Malicious Forensic Data Collection and Exploitation > Wright-Patterson AFB > Article Display
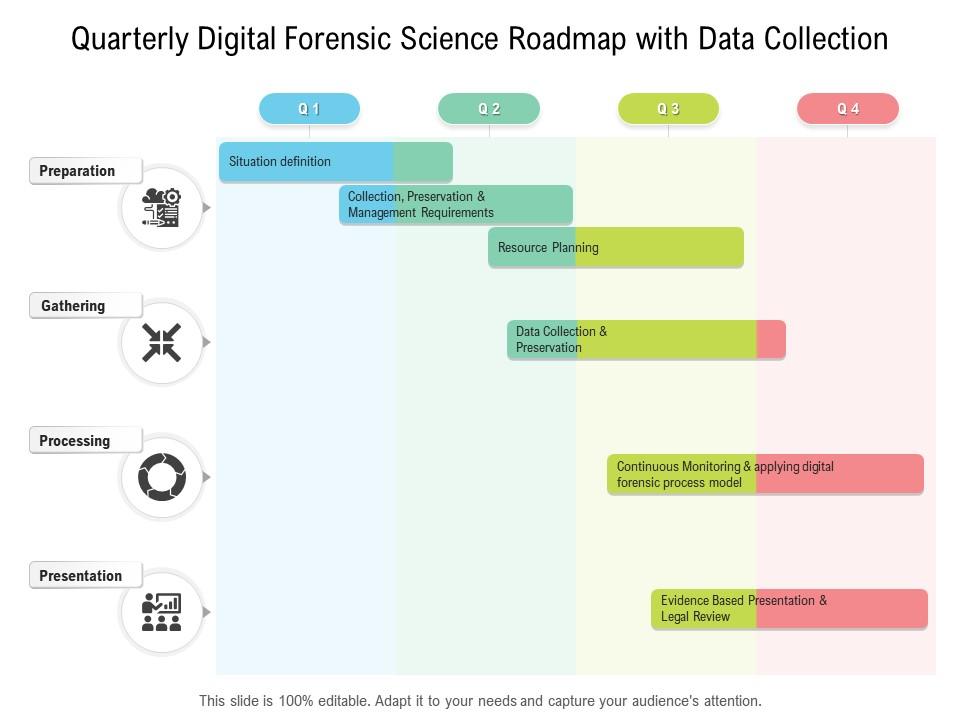
Quarterly Digital Forensic Science Roadmap With Data Collection | PowerPoint Slides Diagrams | Themes for PPT | Presentations Graphic Ideas

Forensic Data Collections 2.0 : The Guide for Defensible & Efficient Processes (Paperback) - Walmart.com

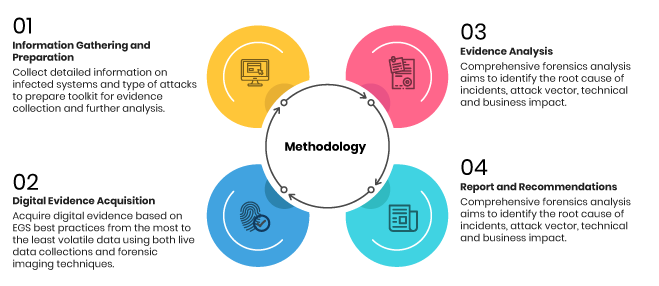
Secrets of Effective Cyber Forensics Investigation and Data Collection | Reserve Bank Information Technology Private Limited (ReBIT)

Linux Malware Incident Response: A Practitioner's Guide to Forensic Collection and Examination of Volatile Data: An Excerpt from Malware Forensic Field Guide for Linux Systems: Malin, Cameron H., Casey BS MA, Eoghan,








.png?width=670&name=MicrosoftTeams-image%20(1).png)